You are here
Technology
Better application networking and security with CAKES
Modern software applications are underpinned by a large and growing web of APIs, microservices, and cloud services that must be highly available, fault tolerant, and secure. The underlying networking technology must support all of these requirements, of course, but also explosive growth.
Unfortunately, the previous generation of technologies are too expensive, brittle, and poorly integrated to adequately solve this challenge. Combined with non-optimal organizational practices, regulatory compliance requirements, and the need to deliver software faster, a new generation of technology is needed to address these API, networking, and security challenges.
3 secrets to deploying LLMs on cloud platforms
In the past two years, I’ve been involved with generative AI projects using large language models (LLMs) more than traditional systems. I’ve become nostalgic for serverless cloud computing. Their applications range from enhancing conversational AI to providing complex analytical solutions across industries and many functions beyond that. Many enterprises deploy these models on cloud platforms because there is a ready-made ecosystem of public cloud providers and it’s the path of least resistance. However, it’s not cheap.
ECMAScript 2024 takes shape
ECMAScript 2024, a planned update to ECMA’s standard for JavaScript, is set to include seven new features ranging from array grouping to Unicode strings. The 2024 specification, from ECMA’s Technical Committee 39, is expected to be approved in June.
Among the list of finished features cited for publication this year is a proposal for array grouping. Motivating this proposal is the notion that array grouping is a common operation best exemplified by SQL’s GROUP BY clause and mapreduce programming. The ability to combine like data into groups lets developers compute higher order data sets.
Crickets from Chirp Systems in Smart Lock Key Leak
The U.S. government is warning that “smart locks” securing entry to an estimated 50,000 dwellings nationwide contain hard-coded credentials that can be used to remotely open any of the locks. The lock’s maker Chirp Systems remains unresponsive, even though it was first notified about the critical weakness in March 2021. Meanwhile, Chirp’s parent company, RealPage, Inc., is being sued by multiple U.S. states for allegedly colluding with landlords to illegally raise rents.
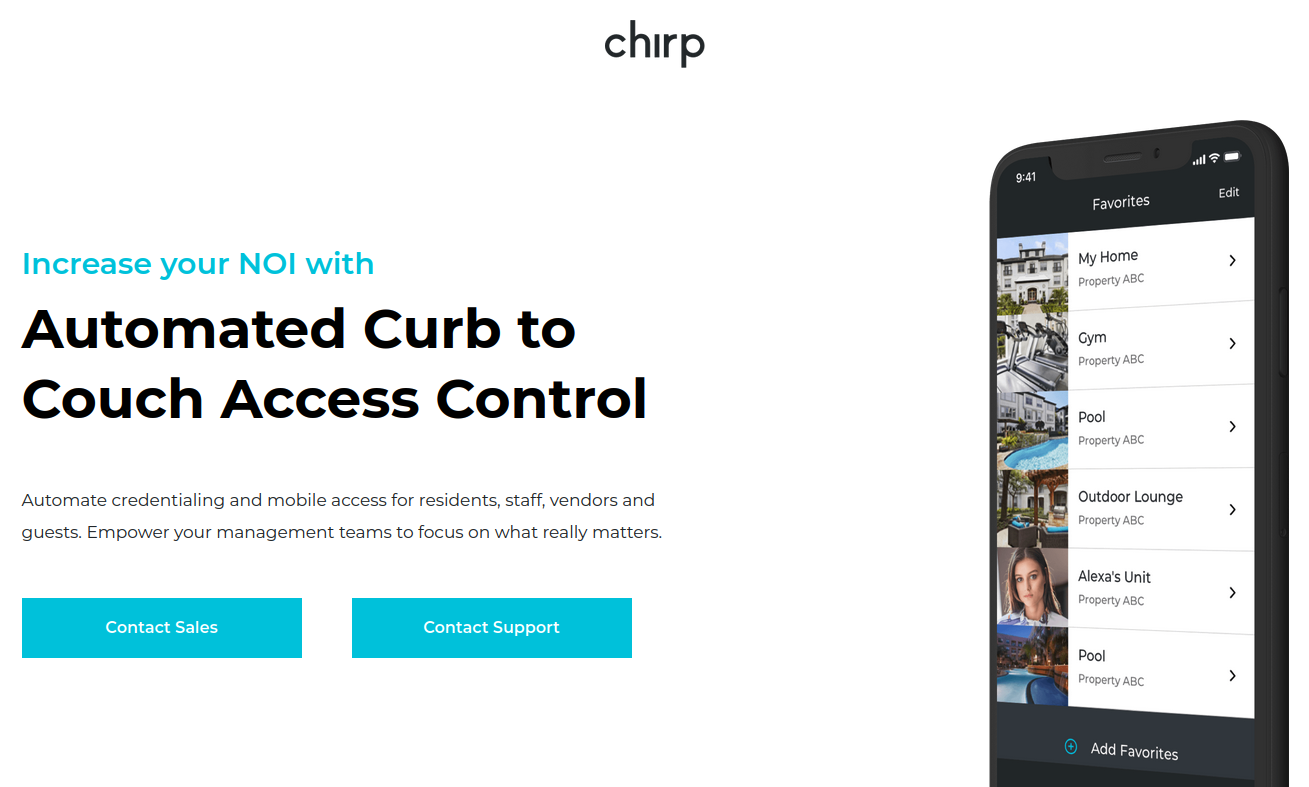
On March 7, 2024, the U.S. Cybersecurity & Infrastructure Security Agency (CISA) warned about a remotely exploitable vulnerability with “low attack complexity” in Chirp Systems smart locks.
“Chirp Access improperly stores credentials within its source code, potentially exposing sensitive information to unauthorized access,” CISA’s alert warned, assigning the bug a CVSS (badness) rating of 9.1 (out of a possible 10). “Chirp Systems has not responded to requests to work with CISA to mitigate this vulnerability.”
Matt Brown, the researcher CISA credits with reporting the flaw, is a senior systems development engineer at Amazon Web Services. Brown said he discovered the weakness and reported it to Chirp in March 2021, after the company that manages his apartment building started using Chirp smart locks and told everyone to install Chirp’s app to get in and out of their apartments.
“I use Android, which has a pretty simple workflow for downloading and decompiling the APK apps,” Brown told KrebsOnSecurity. “Given that I am pretty picky about what I trust on my devices, I downloaded Chirp and after decompiling, found that they were storing passwords and private key strings in a file.”
Using those hard-coded credentials, Brown found an attacker could then connect to an application programming interface (API) that Chirp uses which is managed by smart lock vendor August.com, and use that enumerate and remotely lock or unlock any door in any building that uses the technology.
Brown said when he complained to his leasing office, they sold him a small $50 key fob that uses Near-Field Communications (NFC) to toggle the lock when he brings the fob close to his front door. But he said the fob doesn’t eliminate the ability for anyone to remotely unlock his front door using the exposed credentials and the Chirp mobile app.

A smart lock enabled with Chirp. Image: Camdenliving.com
Also, the fobs pass the credentials to his front door over the air in plain text, meaning someone could clone the fob just by bumping against him with a smartphone app made to read and write NFC tags.
Neither August nor Chirp Systems responded to requests for comment. It’s unclear exactly how many apartments and other residences are using the vulnerable Chirp locks, but multiple articles about the company from 2020 state that approximately 50,000 units use Chirp smart locks with August’s API.
Roughly a year before Brown reported the flaw to Chirp Systems, the company was bought by RealPage, a firm founded in 1998 as a developer of multifamily property management and data analytics software. In 2021, RealPage was acquired by the private equity giant Thoma Bravo.
Brown said the exposure he found in Chirp’s products is “an obvious flaw that is super easy to fix.”
“It’s just a matter of them being motivated to do it,” he said. “But they’re part of a private equity company now, so they’re not answerable to anybody. It’s too bad, because it’s not like residents of [the affected] properties have another choice. It’s either agree to use the app or move.”
In October 2022, an investigation by ProPublica examined RealPage’s dominance in the rent-setting software market, and that it found “uses a mysterious algorithm to help landlords push the highest possible rents on tenants.”
“For tenants, the system upends the practice of negotiating with apartment building staff,” ProPublica found. “RealPage discourages bargaining with renters and has even recommended that landlords in some cases accept a lower occupancy rate in order to raise rents and make more money. One of the algorithm’s developers told ProPublica that leasing agents had ‘too much empathy’ compared to computer generated pricing.”
Last year, the U.S. Department of Justice threw its weight behind a massive lawsuit filed by dozens of tenants who are accusing the $9 billion apartment software company of helping landlords collude to inflate rents.
In February 2024, attorneys general for Arizona and the District of Columbia sued RealPage, alleging RealPage’s software helped create a rental monopoly.
Data pipelines for the rest of us
Depending on your politics, trickle-down economics never worked all that well in the United States under President Ronald Reagan. In open source software, however, it seems to be doing just fine.
I’m not really talking about economic policies, of course, but rather about elite software engineering teams releasing code that ends up powering the not-so-elite mainstream. Take Lyft, for example, which released the popular Envoy project. Or Google, which gave the world Kubernetes (though, as I’ve argued, the goal wasn’t charitable niceties, but rather corporate strategy to outflank the dominant AWS). Airbnb figured out a way to move beyond batch-oriented cron scheduling, gifting us Apache Airflow and data pipelines-as-code.
Beyond Git: How version control systems are evolving for devops
Tools that manage changes to source code, programs, documents, or other collections of information are known by a variety of names: version control, revision control, source control, or source code management are all common descriptors. Regardless of what we call them, these systems have become increasingly vital in a world where software and data are essential commodities.
Demand for version control systemsVersion control systems (VCS) are used to track every change to source code. They help development teams and others manage these changes over time. As market pressures accelerate development efforts to bring products to market faster, version control has become more important than ever.
TWiT 975: You Don't Want to Make Ghandi Mad - AI Music, Broadband Nutrition Labels
- AI Music with Suno and Udio
- Google's DeepMind finds 2.2M crystal structures in materials science win
- Vana plans to let users rent out their Reddit data to train AI
- How I Built an AI-Powered, Self-Running Propaganda Machine for $105
- AI's Victories in Go Inspire Better Human Game Playing
- Why the California Journalism Preservation Act is putting support of the news ecosystem at risk
- Google and the CJPA
- Consumers will finally see FCC-mandated 'nutrition labels' for most broadband plans
- SAG-AFTRA union secures AI protections for artists in deal with major record labels
- Peter Higgs, physicist who proposed Higgs boson, dies aged 94 | Peter Higgs
- BESSY II: How pulsed charging enhances the service time of batteries
Host: Leo Laporte
Guests: Denise Howell, Larry Magid, and Owen Thomas
Download or subscribe to this show at https://twit.tv/shows/this-week-in-tech
Get episodes ad-free with Club TWiT at https://twit.tv/clubtwit
Sponsors:
Rust gets security fix for Windows vulnerability
The Rust language team has published a point release of Rust to fix a critical vulnerability to the standard library that could benefit an attacker when using Windows.
Rust 1.77.2, published on April 9, includes a fix for CVE-2024-24576. Before this release, Rust’s standard library did not properly escape arguments when invoking batch files with the bat and cmd extensions on Windows using the Command API. An attacker who controlled arguments passed to a spawned process could execute arbitrary shell commands by bypassing the escape. This vulnerability becomes critical if batch files are invoked on Windows with untrusted arguments. No other platform or use was affected. Developers already using Rust can get Rust 1.77.2 using the command: rustup update stable.
The cloud is benefiting IT, but not business
“The cloud has tremendous business value!” That’s the battle cry chanted by cloud providers and their allies at every cloud computing conference.
You will never hear me say that “the cloud” is always the right solution or, for that matter, the wrong solution. In my 20-plus years as a cloud expert, I’ve never blindly followed the lead of cloud computing pioneers or adopters. Like any other technology trend and category, cloud computing should be considered on a case-by-case basis.
This balanced approach may have cost me some friends and perhaps some jobs, but I believe this will remain the right way to think about cloud deployments in 2024.
How to implement database connection resiliency in ASP.NET Core
A high-quality application must be stable, performant, scalable, and reliable. The reliability of an application depends on many factors, but one of the most important is resiliency, or the ability to withstand failures or faults during run time. In this article, we’ll see how we can bring resiliency to database connections in ASP.NET Core using Entity Framework Core.
EF Core has a feature called connection resiliency that automatically retries failed database commands to maintain connectivity during transient errors or network instability. By encapsulating the logic for identifying failures and retrying commands, this feature allows us to devise execution plans for different database failure situations.
Microsoft offers SDK for testing framework
Microsoft has announced the MSTest SDK. Built on the MSBuild Project SDK system and based on the MSTest runner, the MSTest SDK is designed to give developers a better experience for testing with MSTest, Microsoft’s framework for unit testing.
The MSTest SDK, announced April 11, makes project configuration easier via sensible defaults and flexible options, Microsoft said. To use the MSTest SDK, developers must create an MSTest project, or update an existing MSTest project, and replace the content of the .csproj file.
JetBrains launches IDE management suite
JetBrains has introduced JetBrains IDE Services, a product suite intended to simplify the management of the company’s IntelliJ-based IDEs, remote development environments, and AI-powered coding assistant. The suite also includes a collaborative programming solution.
Unveiled April 9, JetBrains IDE Services is designed to alleviate the challenges of deploying and overseeing IDEs and other developer tools for large organizations, the company said. JetBrains, which is perhaps best known for its IntelliJ IDEA IDE for Java and Kotlin, has positioned the package as “a central hub for all things IDE.”
Why CISA is Warning CISOs About a Breach at Sisense
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) said today it is investigating a breach at business intelligence company Sisense, whose products are designed to allow companies to view the status of multiple third-party online services in a single dashboard. CISA urged all Sisense customers to reset any credentials and secrets that may have been shared with the company, which is the same advice Sisense gave to its customers Wednesday evening.
New York City based Sisense has more than 1,000 customers across a range of industry verticals, including financial services, telecommunications, healthcare and higher education. On April 10, Sisense Chief Information Security Officer Sangram Dash told customers the company had been made aware of reports that “certain Sisense company information may have been made available on what we have been advised is a restricted access server (not generally available on the internet.)”
“We are taking this matter seriously and promptly commenced an investigation,” Dash continued. “We engaged industry-leading experts to assist us with the investigation. This matter has not resulted in an interruption to our business operations. Out of an abundance of caution, and while we continue to investigate, we urge you to promptly rotate any credentials that you use within your Sisense application.”
In its alert, CISA said it was working with private industry partners to respond to a recent compromise discovered by independent security researchers involving Sisense.
“CISA is taking an active role in collaborating with private industry partners to respond to this incident, especially as it relates to impacted critical infrastructure sector organizations,” the sparse alert reads. “We will provide updates as more information becomes available.”
Sisense declined to comment when asked about the veracity of information shared by two trusted sources with close knowledge of the breach investigation. Those sources said the breach appears to have started when the attackers somehow gained access to the company’s code repository at Gitlab, and that in that repository was a token or credential that gave the bad guys access to Sisense’s Amazon S3 buckets in the cloud.
Both sources said the attackers used the S3 access to copy and exfiltrate several terabytes worth of Sisent customer data, which apparently included millions of access tokens, email account passwords, and even SSL certificates.
The incident raises questions about whether Sisense was doing enough to protect sensitive data entrusted to it by customers, such as whether the massive volume of stolen customer data was ever encrypted while at rest in these Amazon cloud servers.
It is clear, however, that unknown attackers now have all of the credentials that Sisense customers used in their dashboards.
The breach also makes clear that Sisense is somewhat limited in the clean-up actions that it can take on behalf of customers, because access tokens are essentially text files on your computer that allow you to stay logged in for extended periods of time — sometimes indefinitely. And depending on which service we’re talking about, it may be possible for attackers to re-use those access tokens to authenticate as the victim without ever having to present valid credentials.
Beyond that, it is largely up to Sisense customers to decide if and when they change passwords to the various third-party services that they’ve previously entrusted to Sisense.
Earlier today, a public relations firm working with Sisense reached out to learn if KrebsOnSecurity planned to publish any further updates on their breach (KrebsOnSecurity posted a screenshot of the CISO’s customer email to both LinkedIn and Mastodon on Wednesday evening). The PR rep said Sisense wanted to make sure they had an opportunity to comment before the story ran.
But when confronted with the details shared by my sources, Sisense apparently changed its mind.
“After consulting with Sisense, they have told me that they don’t wish to respond,” the PR rep said in an emailed reply.
Nicholas Weaver, a researcher at University of California, Berkeley’s International Computer Science Institute (ICSI) and lecturer at UC Davis, said a company entrusted with so many sensitive logins should absolutely be encrypting that information.
“If they are hosting customer data on a third-party system like Amazon, it better damn well be encrypted,” Weaver said. “If they are telling people to rest credentials, that means it was not encrypted. So mistake number one is leaving Amazon credentials in your Git archive. Mistake number two is using S3 without using encryption on top of it. The former is bad but forgivable, but the latter given their business is unforgivable.”
Xamarin Forms reaches end of life. What should you do?
In less than a month Microsoft will end support for .NET’s first major cross-platform UI tool, Xamarin Forms. Instead of developers having to build separate UIs for Windows, iOS, and Android, Xamarin Forms gave us a set of cross-platform UI controls we could use to build one code base that compiled to all target platforms, without any device-specific code. It was a big hit, but now it’s fading away.
Microsoft has been developing a follow-on to Xamarin Forms in the shape of MAUI, the Multi-platform App UI. MAUI supports Windows, macOS, iOS, and Android, again allowing you to continue to develop code using the same tools and techniques as Xamarin, working with the latest .NET releases. MAUI is still very much under development, with some differences that make it hard to simply swap out one set of controls for another.
Xamarin Forms is dead. Now what?
In less than a month Microsoft will end support for .NET’s first major cross-platform UI tool, Xamarin Forms. Instead of developers having to build separate UIs for Windows, iOS, and Android, Xamarin Forms gave us a set of cross-platform UI controls we could use to build one code base that compiled to all target platforms, without any device-specific code. It was a big hit, but now it’s fading away.
Microsoft has been developing a follow-on to Xamarin Forms in the shape of MAUI, the Multi-platform App UI. MAUI supports Windows, macOS, iOS, and Android, again allowing you to continue to develop code using the same tools and techniques as Xamarin, working with the latest .NET releases. MAUI is still very much under development, with some differences that make it hard to simply swap out one set of controls for another.
Exploring the Apache ecosystem for data analysis
The Apache Software Foundation develops and maintains open source software projects that significantly impact various domains of computing, from web servers and databases to big data and machine learning. As the volume and velocity of time series data continue to grow, thanks to IoT devices, AI, financial systems, and monitoring tools, more and more companies will rely on the Apache ecosystem to manage and analyze this kind of data.
Visual Studio update brings smoother Copilot integration
With the third preview of the planned Visual Studio 2022 17.10, Microsoft has “unified” the GitHub Copilot experience in the IDE, combining Copilot and Copilot Chat into a single extension.
Introduced April 9, Visual Studio 2022 17.10 Preview 3 combines the features of GitHub Copilot and Copilot Chat into one package, eliminating the need to install two separate extensions and will provide a more integrated AI experience in the future, Microsoft said. Developers can activate a GitHub Copilot subscription at github.com.
Six key takeaways from Google Cloud Next ’24
It wouldn’t have taken a billion-parameter large language model (LLM) to predict that the dominant theme of this year’s Google Cloud Next conference would be generative AI—indeed, it will probably be the dominant theme of the year for most enterprise software developers.
At the event, Google introduced a host of updates to its cloud platform to make working with LLMs easier, and added generative AI-based assistants to many of its offerings. Here are six key takeaways from the conference:
Twitter’s Clumsy Pivot to X.com Is a Gift to Phishers
On April 9, Twitter/X began automatically modifying links that mention “twitter.com” to read “x.com” instead. But over the past 48 hours, dozens of new domain names have been registered that demonstrate how this change could be used to craft convincing phishing links — such as fedetwitter[.]com, which until very recently rendered as fedex.com in tweets.
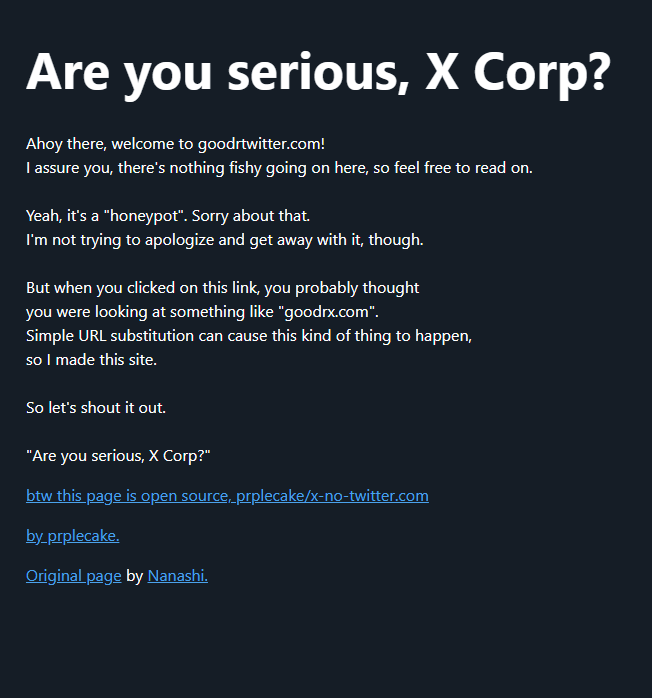
The message displayed when one visits carfatwitter.com, which Twitter/X displayed as carfax.com in tweets and messages.
A search at DomainTools.com shows at least 60 domain names have been registered over the past two days for domains ending in “twitter.com,” although research so far shows the majority of these domains have been registered “defensively” by private individuals to prevent the domains from being purchased by scammers.
Those include carfatwitter.com, which Twitter/X truncated to carfax.com when the domain appeared in user messages or tweets. Visiting this domain currently displays a message that begins, “Are you serious, X Corp?”
Update: It appears Twitter/X has corrected its mistake, and no longer truncates any domain ending in “twitter.com” to “x.com.”
Original story:
The same message is on other newly registered domains, including goodrtwitter.com (goodrx.com), neobutwitter.com (neobux.com), roblotwitter.com (roblox.com), square-enitwitter.com (square-enix.com) and yandetwitter.com (yandex.com). The message left on these domains indicates they were defensively registered by a user on Mastodon whose bio says they are a systems admin/engineer. That profile has not responded to requests for comment.
A number of these new domains including “twitter.com” appear to be registered defensively by Twitter/X users in Japan. The domain netflitwitter.com (netflix.com, to Twitter/X users) now displays a message saying it was “acquired to prevent its use for malicious purposes,” along with a Twitter/X username.
The domain mentioned at the beginning of this story — fedetwitter.com — redirects users to the blog of a Japanese technology enthusiast. A user with the handle “amplest0e” appears to have registered space-twitter.com, which Twitter/X users would see as the CEO’s “space-x.com.” The domain “ametwitter.com” already redirects to the real americanexpress.com.
Some of the domains registered recently and ending in “twitter.com” currently do not resolve and contain no useful contact information in their registration records. Those include firefotwitter[.]com (firefox.com), ngintwitter[.]com (nginx.com), and webetwitter[.]com (webex.com).
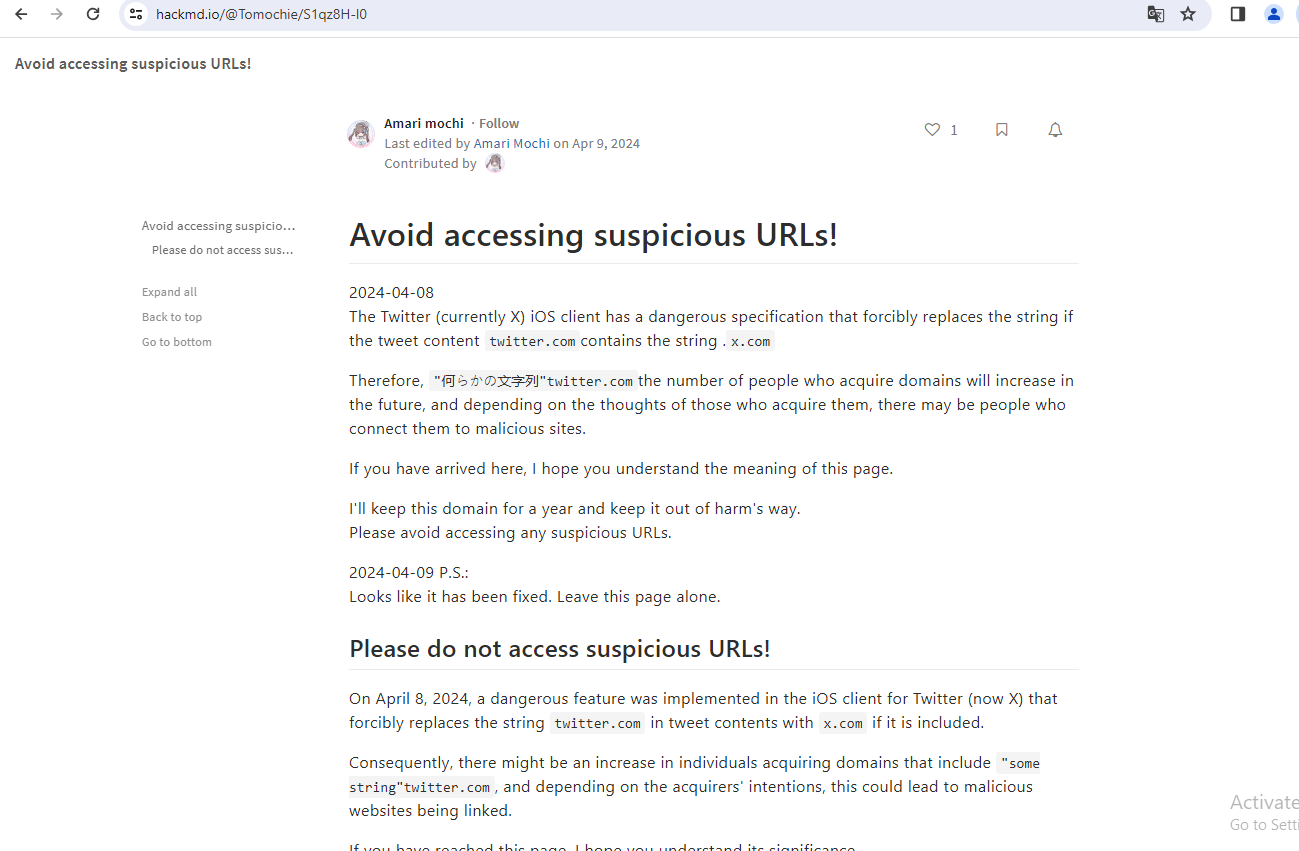
The domain setwitter.com, which Twitter/X until very recently rendered as “sex.com,” redirects to this blog post warning about the recent changes and their potential use for phishing.
Sean McNee, vice president of research and data at DomainTools, told KrebsOnSecurity it appears Twitter/X did not properly limit its redirection efforts.
“Bad actors could register domains as a way to divert traffic from legitimate sites or brands given the opportunity — many such brands in the top million domains end in x, such as webex, hbomax, xerox, xbox, and more,” McNee said. “It is also notable that several other globally popular brands, such as Rolex and Linux, were also on the list of registered domains.”
The apparent oversight by Twitter/X was cause for amusement and amazement from many former users who have migrated to other social media platforms since the new CEO took over. Matthew Garrett, a lecturer at U.C. Berkeley’s School of Information, summed up the Schadenfreude thusly:
“Twitter just doing a ‘redirect links in tweets that go to x.com to twitter.com instead but accidentally do so for all domains that end x.com like eg spacex.com going to spacetwitter.com’ is not absolutely the funniest thing I could imagine but it’s high up there.”